The Role of CVE in Patch Management
The CVE Program identifies, defines, and catalogs publicly disclosed information security vulnerabilities. IT and cybersecurity professionals use CVE and the corresponding Common Vulnerability Scoring System (CVSS) score to prioritize patching strategies.
While CVSS scores and CVE are helpful, they do not fully address vulnerability management challenges. This gap can leave organizations vulnerable to untreated risks and attacks.
Identifying Vulnerabilities
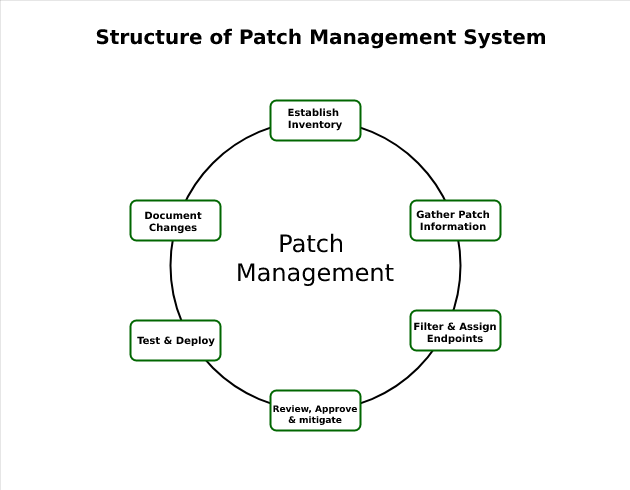
Vulnerabilities that have not been patched on a timely basis are among the most common reasons for data breaches. To prevent these types of breaches, organizations need to identify and prioritize vulnerabilities. The CVE program is an important tool for this process.
Its goal is to provide an open-source platform for recognizing, tracking and cataloging publicly disclosed cybersecurity vulnerabilities. The program helps software developers, security professionals, and end users understand how to protect their systems from these threats.
Once a vulnerability is reported to one of the CNAs, it receives a unique ID and is then published to the public. Each entry includes a brief description of the vulnerability, a list of references containing additional reports, and more. These entries are constantly updated as new information comes to light.
Anyone can report a vulnerability to a CNA, including researchers and white hat hackers. Many vendors also offer bug bounties to encourage people to seek out and report security flaws in their products. These vulnerabilities can then be categorized and assigned a CVSS score, which allows companies to plan risk management strategies and prioritize their patching schedules accordingly.
The CVSS score determines how serious a particular vulnerability is and what priority it should be given. This is why it is essential to have a well-established patch management process in place.
Prioritizing Vulnerabilities
When a researcher or company discovers a new vulnerability, it’s added to the CVE list. Each entry includes a standardized name, a short description and a reference section that lists additional information. This enables researchers who scan for vulnerabilities to find the relevant information quickly and easily. The CVE system is used for all forms of software, including finished products, pre-release versions and betas — provided they have been made public.
It’s important to note that not all CVEs are created equal, and the most severe ones should receive your highest priority. A vulnerability’s severity is determined by its Common Vulnerability Scoring System (CVSS) score, which runs from 0 to 10. A higher CVSS means a more severe risk.
A streamlined patch management process requires that you first classify each vulnerability based on its impact, probability of exploitation and sensitivity. This allows you to prioritize which vulnerabilities need remediating first, such as the most critical assets in your organization or those with the highest likelihood of being targeted by threat actors.
Once you have classified each vulnerability, it’s a good idea to compare them against your asset inventory, which will help you assess the potential impact and prioritize remediation. This may require the creation of a test environment that closely matches your production assets, but this is not always possible. Instead, some organizations use a representative sample of their asset inventory.
Deploying Vulnerability Fixes
Using patch management to deploy vulnerability fixes is an essential component of a strong cybersecurity strategy. Promptly applying patches reduces risk, improves system stability, and prevents costly data breaches. Moreover, it ensures compliance in industries like finance and healthcare that must meet regulatory requirements for software security and helps to maintain a positive reputation by showing customers and stakeholders that your business is proactive about protecting their assets.
The CVE process is a valuable resource that helps to keep track of vulnerabilities by providing a common identification scheme. Without it, different databases would use their own IDs, making it difficult to share information between tools.
When a researcher or white-hat hacker discovers a vulnerability, they submit it to the CVE team. This allows them to announce the issue publicly, which puts pressure on vendors to address the problem. CVE also reviews the submission to determine if it meets certain criteria, including references (which includes vendor advisories and proof of concepts), impact, root cause, and solutions such as patches and workarounds.
As part of the patch management process, admins should compare reported vulnerabilities against their inventory to identify gaps and assess their security posture. Prioritizing these vulnerabilities based on their criticality helps to ensure that patches are deployed promptly so that systems remain safe from exploitation. However, it’s important to test these patches before rolling them out in production environments to ensure they don’t introduce any issues with applications or devices.
Monitoring Vulnerabilities
When a patch is released, it’s crucial that an organization quickly test and deploy the new software version to its assets. A delay in the patching process leaves hackers plenty of time to exploit unpatched assets and launch attacks like the 2017 WannaCry ransomware outbreak that impacted organizations across 150 countries.
The CVE system helps organizations identify vulnerabilities and manage patching through a consistent approach to tracking, naming and communicating issues. Even if a company already has systems in place for finding, cataloging and managing vulnerabilities, CVE is an invaluable tool that makes the whole process more streamlined.
As its name implies, the CVE list includes only publicly known security exposures and vulnerabilities. While some critics complain that disclosing a vulnerability on the public list gives hackers an advantage, most infosec professionals agree that the benefits outweigh the risks.
A CVE record includes information such as a description of the problem, its impact and whether it affects hardware or software. In addition, the record provides a unique ID that connects all other resources related to the vulnerability. The database is maintained by the MITRE Corporation, a not-for-profit that operates research and development centers sponsored by the U.S. federal government including the Cybersecurity and Infrastructure Security Agency and the Department of Homeland Security.
In addition to the CVE website, vendors and other third-party sources publish lists of CVEs ordered by the Common Vulnerability Scoring System (CVSS), which assigns a priority level to each vulnerability based on its severity. The system also encourages vendors to offer bug bounties, which reward developers for finding and reporting software bugs.


